Ethereum: Exploring the Differences Between Multi-Signature and Shamir’s Secret Sharing
The Ethereum network, built on the blockchain protocol, has evolved to support various cryptographic techniques for secure data transmission and storage. Two fundamental methods used in this context are multi-signature and Shamir’s secret sharing. While both share similar goals – to ensure the confidentiality, integrity, and authenticity of encrypted data – they differ significantly in their underlying algorithms and implementation approaches.
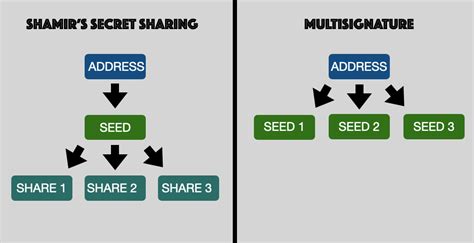
Multi-Signature
A multi-signature scheme is a cryptographic technique that requires multiple parties (signers) to collectively sign and send an encrypted message or data package. This approach ensures that only when all signers have verified the recipient’s identity and agreed upon the content can the data be accessed, transmitted, or stored.
To illustrate this concept, consider a scenario where you want to transfer a cryptocurrency from one wallet address to another. If each of your recipients signs for the transaction using their own private key, the sender must verify that all signers agree on the recipient’s identity and the transaction details before proceeding with the transfer. This requires a significant amount of computational power, making multi-signature schemes suitable for secure transactions where high security is required.
Shamir’s Secret Sharing
Shamir’s secret sharing (SSS) is an encryption technique developed by computer scientist Eli Shamir in 1985. It allows a set of users to share their data securely with specific levels of access, based on their participation in the process. The SS algorithm ensures that only those authorized can recover the original data or perform specific operations.
The basic idea behind SSS is to divide the data into pieces (called shares) and assign each user an appropriate number of shares based on their participation level. When a user wants to access a share, they use their secret key corresponding to the particular share they need. Shamir’s algorithm provides strong security guarantees for sharing data with specific users.
Key Differences
While both multi-signature and SSS aim to protect sensitive information from unauthorized access, there are critical differences between them:
- Computational Requirements: Multi-signature schemes require significant computational resources (e.g., the power consumption of a server) to verify recipient identities before allowing access to data. Shamir’s secret sharing, on the other hand, uses mathematical complexity and does not demand substantial computation.
- Data Security and Integrity: Both techniques provide robust security guarantees; however, SSS inherently includes protection for specific user roles within the data sharing process. Multi-signature schemes often need to be designed around more complex algorithms that can handle high levels of complexity.
- User Roles and Permissions: Shamir’s secret sharing typically supports a hierarchical permission system based on user participation in the data sharing process. This means users have access to specific shares or parts of the shared data as per their role within the system.
Choosing Between Multi-Signature and SSS
The choice between multi-signature and Shamir’s secret sharing ultimately depends on your specific use case:
- Security Requirements: If you need extremely high levels of security, such as access to encrypted financial transactions or sensitive government information, consider using a more complex algorithm like Shamir’s secret sharing.
- User Role-Based Access Control: For data sharing applications that require user roles and permissions (e.g., corporate networks), Shamir’s secret sharing is likely a better fit due to its support for hierarchical role-based access control.
3.